Personal Security Policy | Protect your digital life with 3 easy tips.

For most people it is common to be versed or at least aware of your organizations cyber security policy as part of ongoing security awareness training efforts, but in many cases, that knowledge is only applied in the workplace. What about your personal cyber security policy? Do you have one? Do you follow it? If you answered no to any of the questions above, I am here to help.
Your digital profile should be considered an asset much like the items of value in your home. Maybe more valuable since theft of your identity can potentially result in loss of your tangible assets. Additionally, the means by which your identity or digital assets are stolen typically reside within your house in the form of the electronic devices used to access the internet. Luckily there are some fairly simple precautions and best practices that you can use to fortify yourself against such threats. In the sections that follow, I will go over some of the most common best practices to defend all of your online accounts and assets from compromise.
Password Security
Passwords are typically the first line of defense against an attacker that is after your goods, but not all passwords are good [enough]. Below is a list of recommendations that should be followed when choosing a password as well as best practices for passwords in general.Also, check out my password best practice article.
- Always use strong passwords: Passwords should be at least 14 characters and never consist of words found in the dictionary (in any language). It is best to use ‘passphrases’ rather than ‘passwords’ and to include upper/lower case, numbers and special characters. An example could be: T@k3me0utToth3B@llgam3
- Never re-use passwords: Every account that you have should have a unique and strong passphrase that is not easily guessed by an attacker.
- Never share your passwords: This seems like a no-brainer, but there are plenty of people that share things like their Netflix passwords with friends. While this seems like it may be innocent, if you use the same password (see ‘Never re-use passwords’ above) for Netflix that you use for your bank account, you have just given out your banking password(s) as well.
- Use a password manager: A password manager can help you generate strong passwords as well as maintain those passwords in a secure, central location. This allows you to create long, complex passwords (not even passphrases, just random strings) that you don’t have to remember. It is also convenient as most password managers have browser plugins that allow them to auto-fill login forms. One of my favorites is BitWarden.
- Change passwords periodically: Company’s typically force employees to change their passwords periodically to ensure that the user as well as the company is protected against compromise. This is no different for your personal passwords. I recommend changing your passwords at least yearly. Some password managers have features that can do this for you ‘automagically’ but any password manager will help with this task.
- Use multi-factor authentication: Multi-factor authentication is a means to add a second method of authorization to the login process. Typically, this is done with either and SMS message containing a 6 digit code or using an authenticator app (Google authenticator is a popular app). This has to be configured within each account (such as Facebook or your bank) as well as on the authenticator app itself and is one of the most powerful means to protect your account in conjunction with strong passwords and good password management practices.
Email Security
Another aspect of your digital life that is very important to be security minded about is your email. It is estimated that 90+ percent of email today is SPAM, and that phishing emails are the top attack vector against individuals and companies that suffer a compromise. The reason for this is that everyone has an email account and uses it extensively for communications. Attackers capitalize on this and send massive amounts of SPAM and phishing emails, playing ‘a numbers game’ in which they do not target individuals necessarily but rely on the principal of quantity over quality. Of the thousands of emails that they send, they are likely to get at least a few targets to bite and fall victim to their scam. Here are some best practices to avoid becoming a victim.
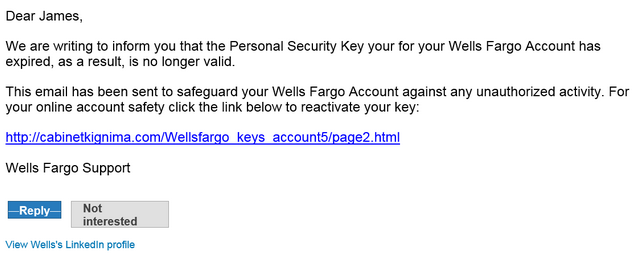
- Click with caution (links): This may seem obvious, but it is the most widely used tactics of an attacker. Planting a link to a piece of malicious code in an email and convincing a user to click on it can give the attacker complete control of your computer and the data on it. This is referred to as ‘phishing’ and can lead to complete compromise. Attackers use enticing (sometimes scary or urgent) language or instill a sense of fear/urgency in the victim to convince them to click a link and it is all down hill from there. Make sure you inspect links before clicking them and look for ‘too good to be true’ language. Hovering over the link without clicking it is also helpful to inspect the actual URL.
- Trust no one: Even if you receive an email from a friend (or an email that appears to be from a friend or other trusted source) be suspicious. Inspect any links in the email before clicking on them. This can be done by hovering your mouse over the link and seeing if it looks like a legitimate URL. You can also look closely at the senders email address and ensure it is in fact from a trusted source. Lastly, most attackers will not sound like your friend. Look for obvious signs in the message that this could be someone impersonating the sender.
Phishing email example:
Open Source Intelligence
OSINT (Open Source Intelligence) while not exactly an asset, it is something that should be closely watched as well. Giving away too much information about yourself can be dangerous and assist an attacker when targeting you. This is hard to do today since everyone is on social media, which by it’s nature is all about sharing information about oneself. Here are some examples of what to watch out for.
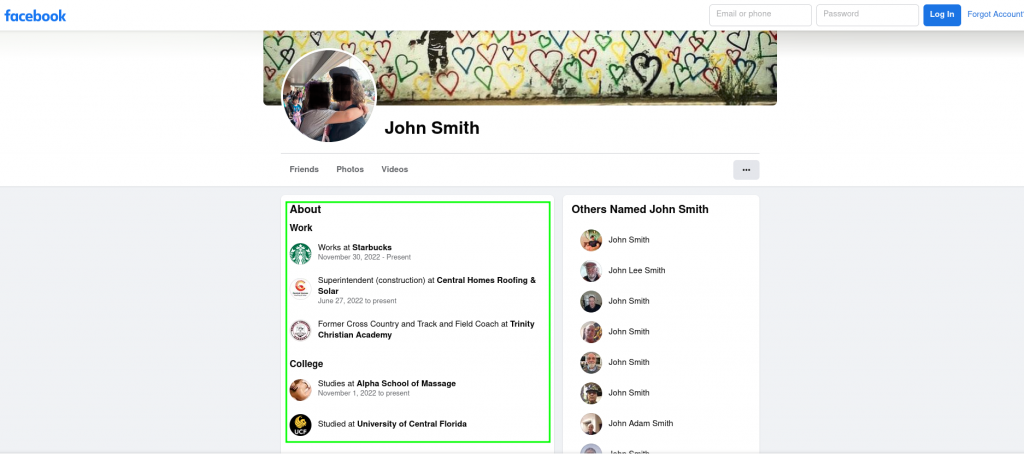
- Security questions: Security questions are a common (and terrible) means to authenticate yourself if you need to reset a password or log into a bank account. If you chose ‘What is your favorite pets name?’ as a security question for example, and you posted on Facebook “my dog fluffy is the cutest pet ever!”, well you just gave away the answer to your security question. Don’t use security questions wherever possible!
- Public information: Public information is valuable to an attacker and often used in targeted attacks, such as ‘spear phishing’ (targeted phishing campaigns), in which an attacker carefully crafts a very convincing email that contains information that is true and relevant, but also available to anyone with the desire to find it. An example could be “A lien has been placed against the home at 101 main street, Plano, TX 52943. Click the link below to see the lien documents and confirm receipt of this urgent email“. Assuming your address is correct (public record) you may be tempted to click the link, and that could lead to compromise.
OSINT example (Too much info on public Facebook page)
Conclusion
The world has changed drastically. The days of protecting your assets by locking your doors at night are over. In the digital age in which we find ourselves, would be thieves can steal much more than your T.V. without ever setting foot on your property. If you implement the three topics above and apply these principals to all aspects of your digital life, you will be in a really good position to avoid potential compromise.